WAF Guide: Attack, Defense, and Deployment Strategies
 Back
Back
As cloud service technology advances and personal mobile devices become popularized, most B2C enterprises have provided cross-platform Web Service to cater to consumer habits. However, as the digitization of enterprises grows, so does the frequency of malicious attacks. The priorities of enterprise cybersecurity are now focused on monitoring, analysis of abnormal traffic and initiating blocking measures.
Currently, the mainstream solutions include defensive CDN services that can accelerate websites and mitigate DDoS attacks. Amongst the services rendered, the use of highly flexible, adaptive and operable WAF firewall requires correct strategies and skills to master.
However, do you truly understand WAF rules? How to monitor traffic in real-time, determine attack patterns based on request contents, set blocking rules, and mitigate the attack pressure without affecting normal services? Let cybersecurity experts teach you the know-how!
Understanding Network Threats Before Using WAF Rules
There are two main purposes of malicious attacks: service interruption and intrusion.
DDoS Attacks: Disrupting Services with Botnets
Denial of service attack is to inundate bandwidth with large amounts of traffic, or overload databases or servers with mass amounts of requests, preventing the victim (target) from providing services, the objective being to either attacking the victim (target)’s interests or to black mail the victim (target).
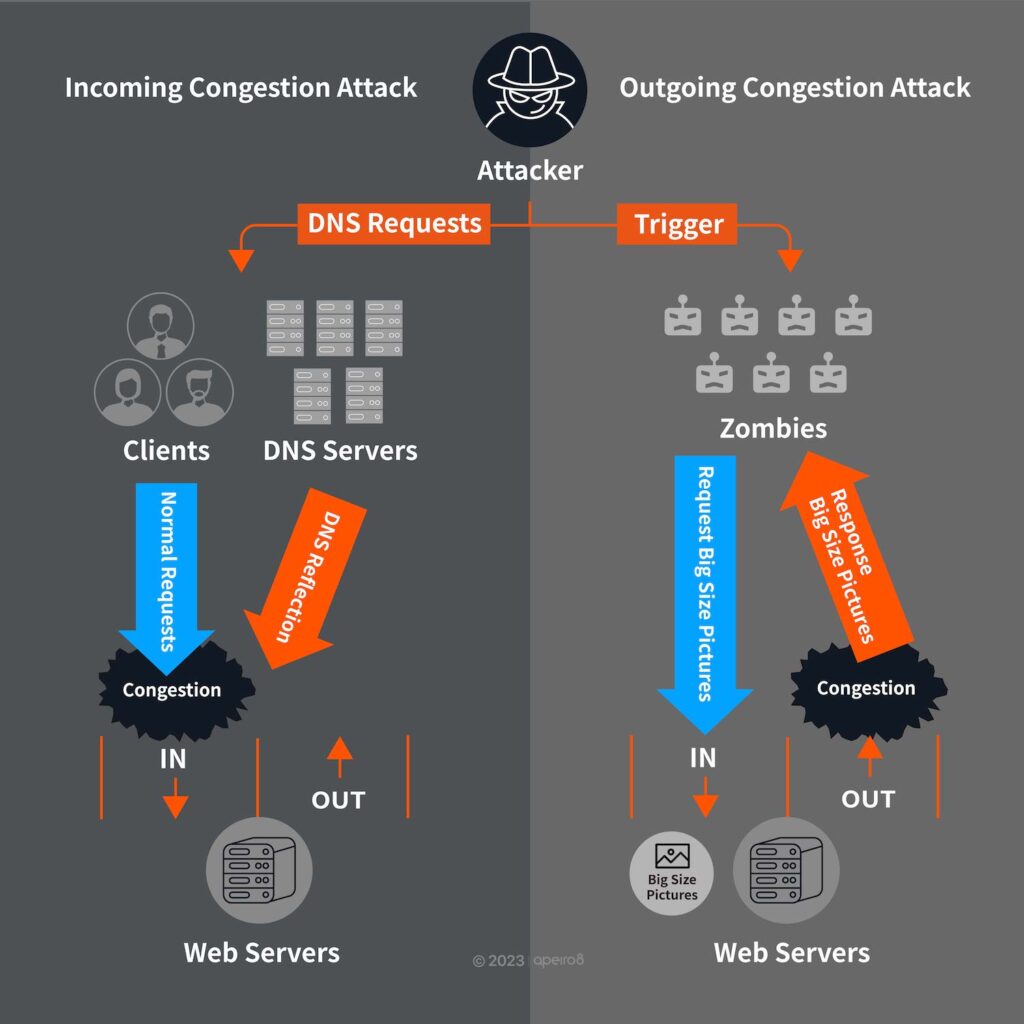
Bandwidth congestion can be achieved either with large packets generating large incoming traffic, or by requesting specific components on the service websites (e.g. back ground picture) to generate large amounts of outgoing traffic from the servers, blocking the outgoing bandwidth.
⬛ Recommend: What is DDoS Attack? Definition, Attack Types, and OSI Model
Incoming congestion attack: attackers mostly use infected zombie equipment or reflection/amplification attacks to create large amounts of traffic, resulting in L3 (such as ICMP flooding) and L4 (such as DNS amplification attack) attacks. To tackle these attacks head-on will require bandwidth costs.
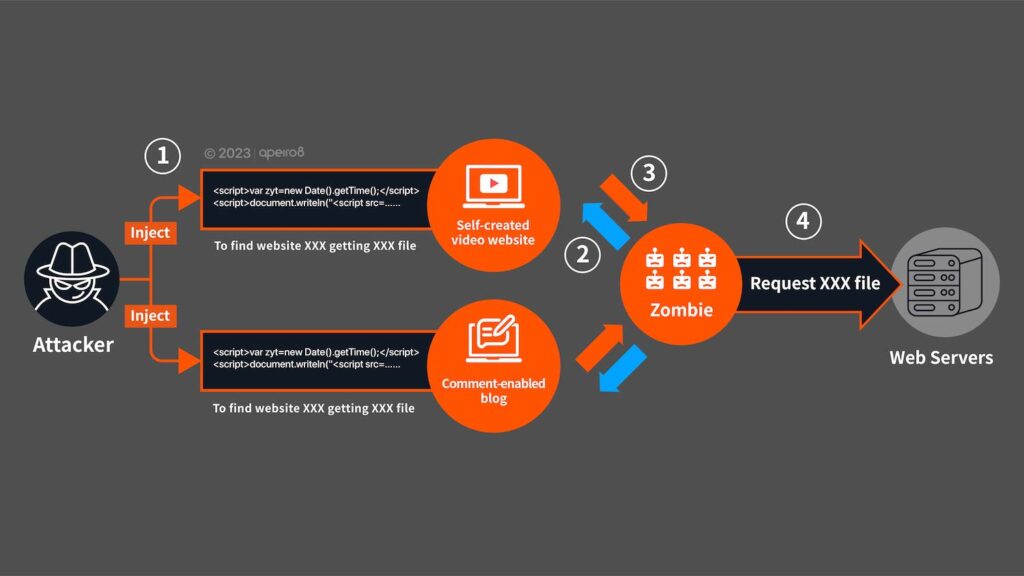
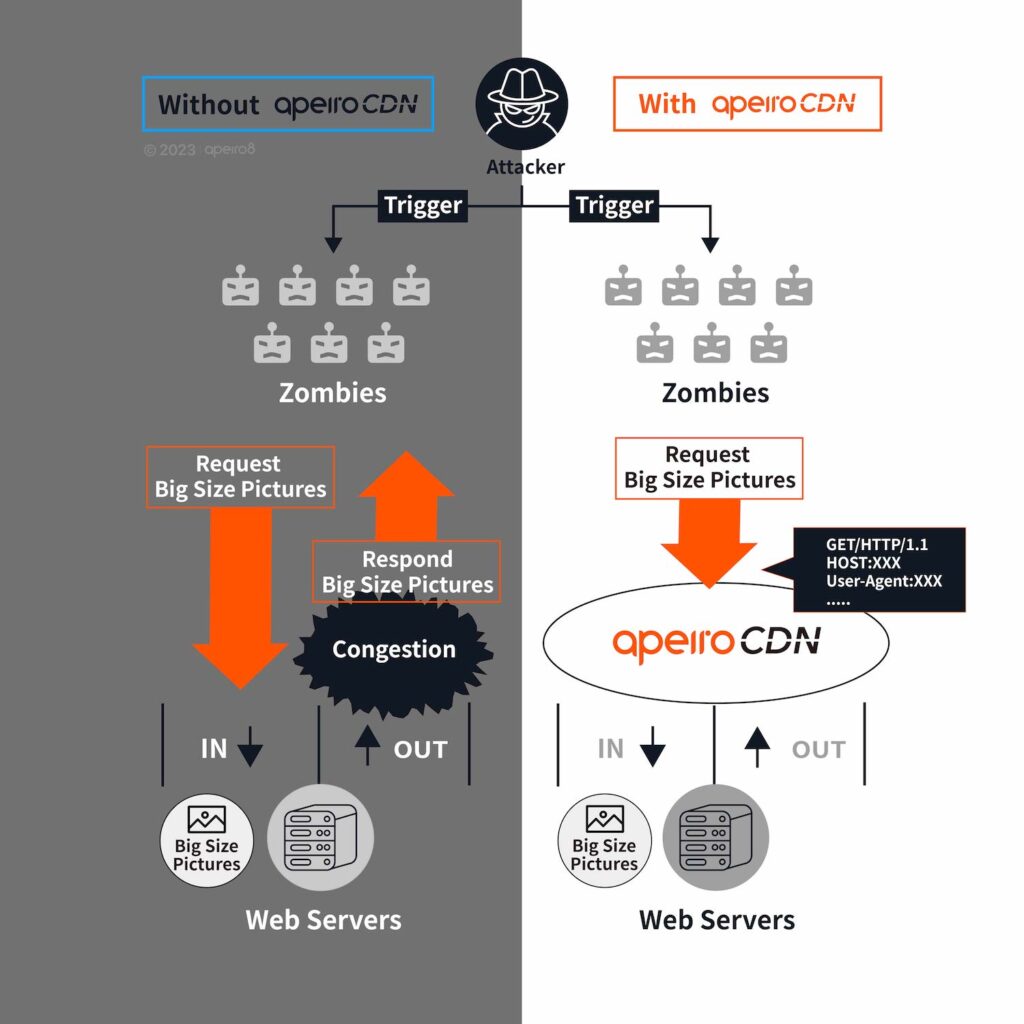
Outgoing congestion attack: attackers mostly use infected zombie equipment to initiate large amounts of requests, or exploit service website vulnerabilities to inject malicious Java script programs. Another way is to create a website that can attract users to stay longer periods of time (such as free online movies or pornographic websites), then to hide malicious programs in it to turn users into zombies, sending large amounts of requests to the intended target in a “stepping attack” fashion.
⬛ Recommend: DDoS Attacks: Top 6 Cost-Effective DDoS Solutions by CDN
Covert “Service Intrusion Attack”: Data Theft and Manipulation
Unlike the overtly conspicuous denial of service attack, “Service Intrusion” operates like espionage, aiming to remain undetected. It bypasses the security verification mechanism of the platform and penetrates the system to steal or tamper data, such as: SQL injection and XSS.
- SQL Injection: Unauthorized Account Access without Password
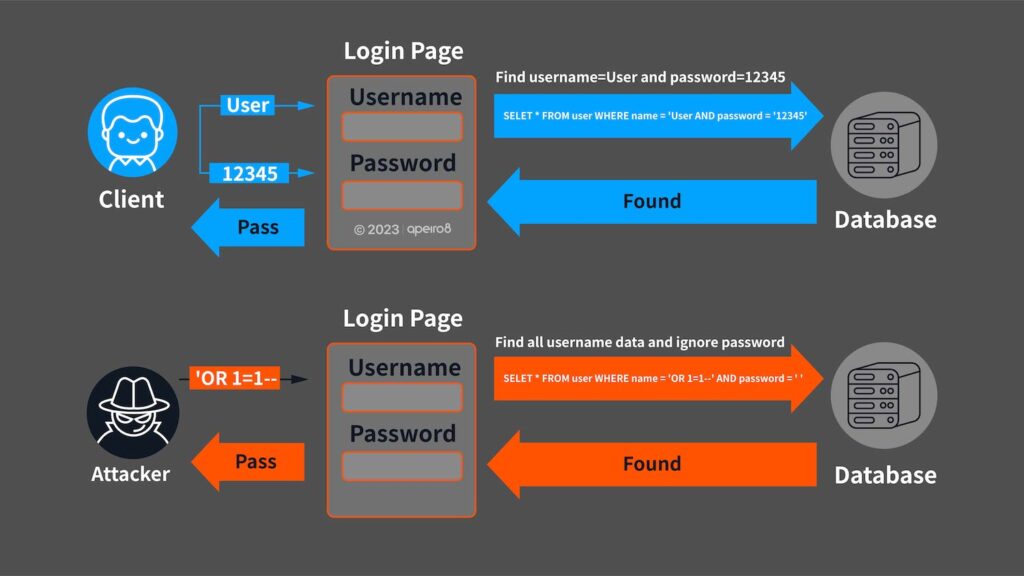
SQL injection is a technique that exploits programming vulnerabilities by injecting SQL code into a request, attempting to retrieve information or modify the contents of a database. For example, in a website’s login page where users input their username and password, the input is used in a query to the database, as shown below:
SELECT * FROM user WHERE name =’username ‘ AND password = ‘ password’ (Search the record where name=username and password=password)
But if the attacker enters ‘OR 1=1 — in the account field, then the query will be:
SELECT * FROM user WHERE name =”OR 1=1 — ‘ AND password = ‘ password'(Return all name fields)
This will allow the attacker to log in the page without entering the password.
Depending on the extant of website vulnerabilities, the attacker may skip over verification and add/modify/delete contents form the database, causing significant losses.
- XSS Attack Enables Unauthorized Website Login
Malicious programs are written for programs run on a user’s browser (such as Java script), followed by social engineering to deceive the user from accessing website containing malicious codes, or use website vulnerabilities to inject attack codes to obtain user information or cookies; all of which will allow attacker to enter the target website by impersonating as logged-in user. As mentioned previously, the user is then tricked into sending large amounts of request to paralyze the victim websites.
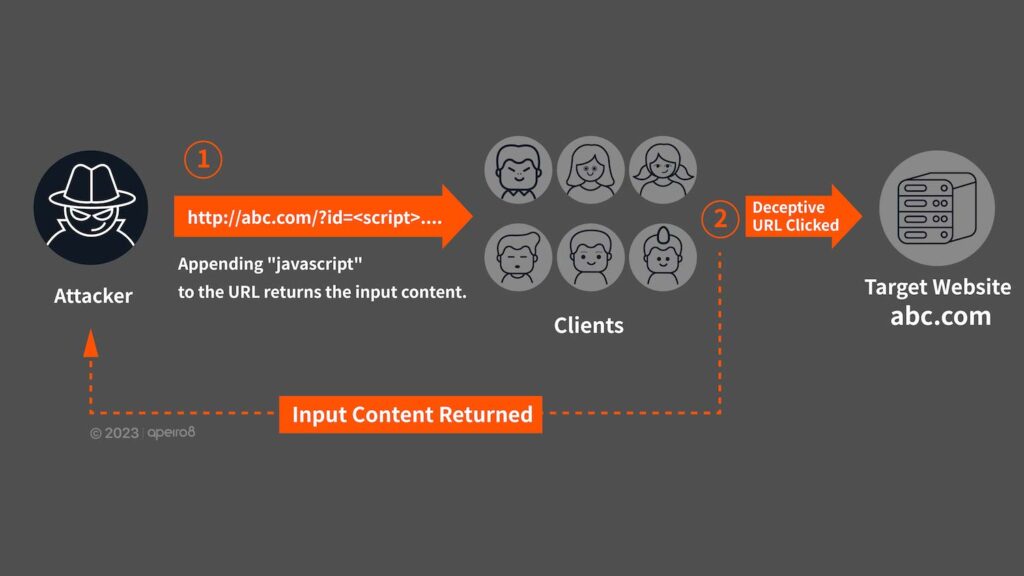
⬛ Recommend: WAF (Web Application Firewall) vs. Firewall: Explained
WAF and CDN Defense Strategies
Distributed IP addresses alleviates L3/L4 Attack Traffics
For L3/L4 type DDoS attacks, the most effective mitigation is to distribute the service IPs to different locations with a CDN provider, which will disperse the attack traffic.
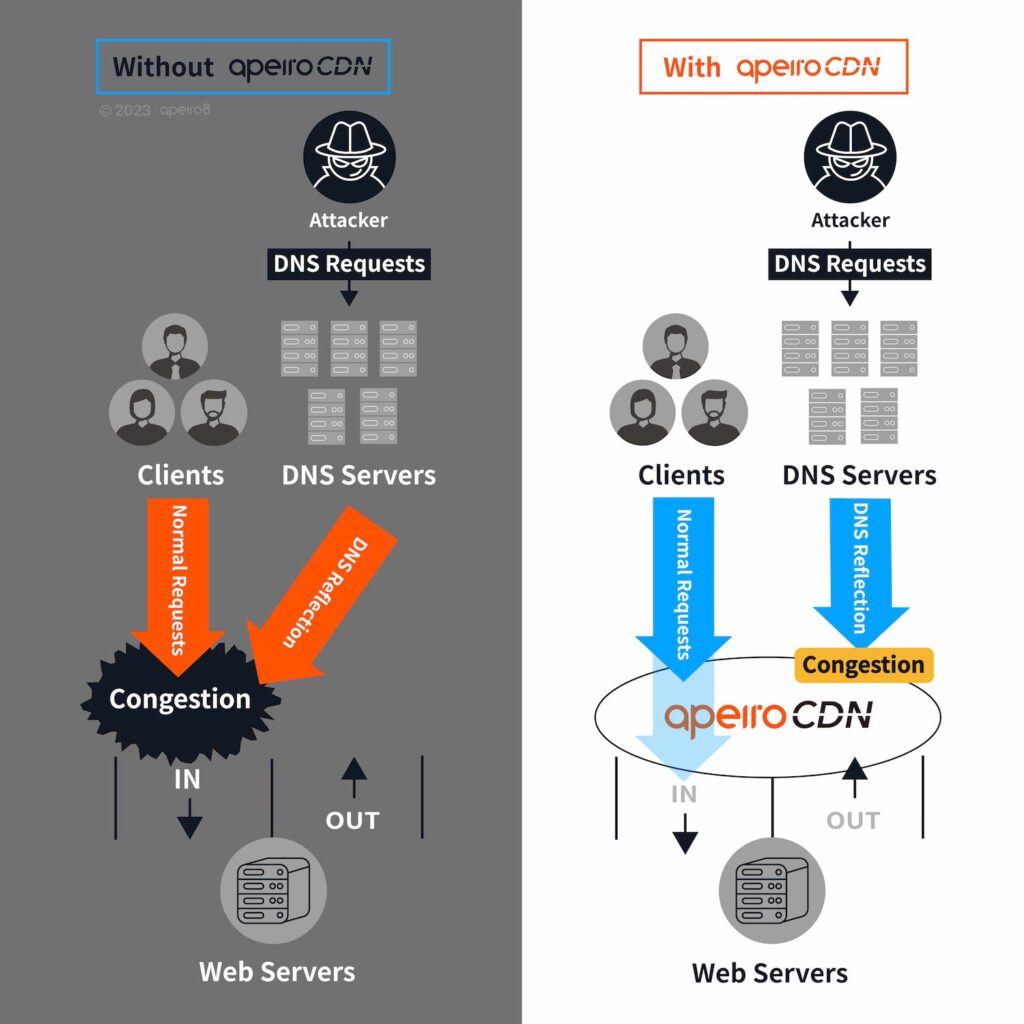
Combat L7 Attacks with Enhanced Authentication and WAF Rules
For L7 multi-request attacks, since the website of every service provider differs from each other, administrators will require the use of systems like WAF to collect information from Layer 7 and compare it to the website behaviors of their own, and then to determine whether the request originates from normal user or malicious attack. For intrusion attack that targets website vulnerabilities like SQL injection or XSS, it is essential that web designers enhance the verification mechanism of the public pages, then configure WAF rules in the server frontend to prevent any possible leaks.
⬛ Recommend: CDN Architecture: Exploring Different Architectures and Benefits
Adapting WAF Rules for Unpredictable Attack Patterns
Cybersecurity is a constant battle with enemies in the dark. As website services continue to update to meet the preferences of users, cybersecurity must also adjust dynamically to rely less on automated system decision.
For incoming attackers, the administrators (CDN monitoring center) must analyze the real-time traffic status and request contents to determine whether the opponent is a bot or normal user; rather than blocking all incoming traffic, administrators need to use other mitigation methods to reduce the stress of attack as much as possible without affecting services.
⬛ Recommend: Exploring Botnets: Mechanisms, Varieties & Defense Strategies
WAF: Reduce False Positives, Handle Various Suspicious Traffic
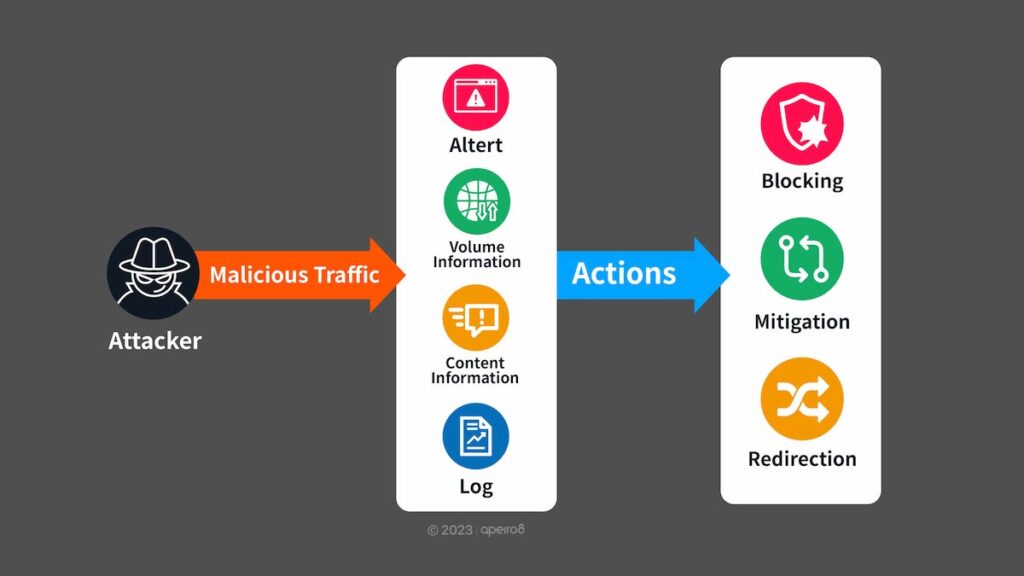
Based on years of protection experience, ApeiroCDN has created a flexible and easy to use WAF system, able to customize defensive strategies based on request headers, countries of origin and frequency detection.
Depending on the request signature types, the defensive actions provided measures other than direct blocking, such as bandwidth restriction, block period (penalty time) and customized responses, all designed to maintain as much availability of the services as possible.
Simultaneously, ApeiroCDN provides trend analysis for domain requests, source IP and response status codes, quality analysis on the latency of “CDN-origin server”, and event log query that includes request headers. Additionally, the system allows customizable alerts based on log contents and trigger threshold values, providing administrators (CDN monitoring center) comprehensive analysis information and firm grasp of service status.
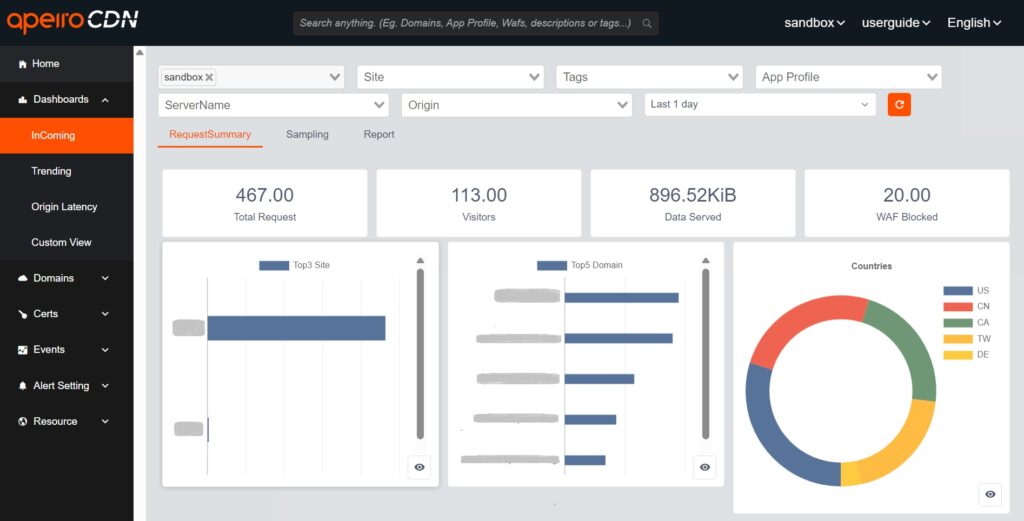
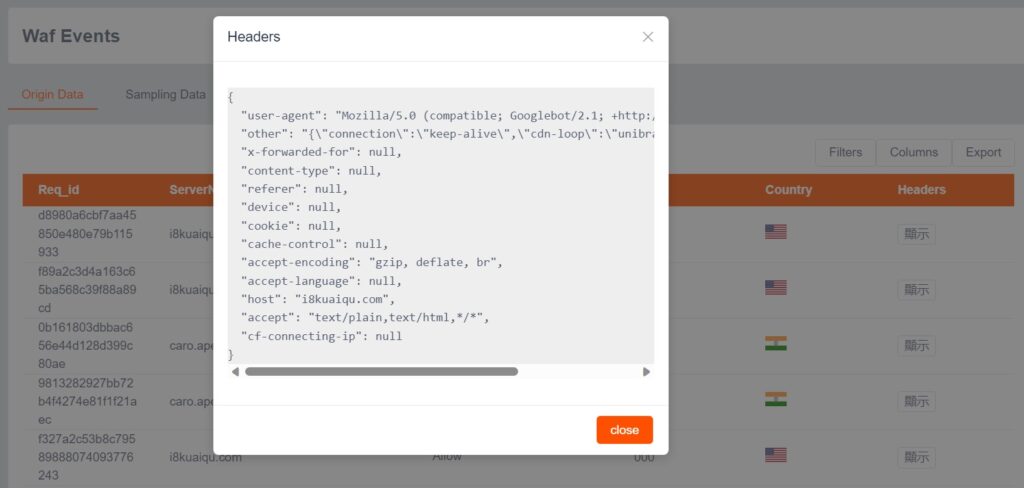
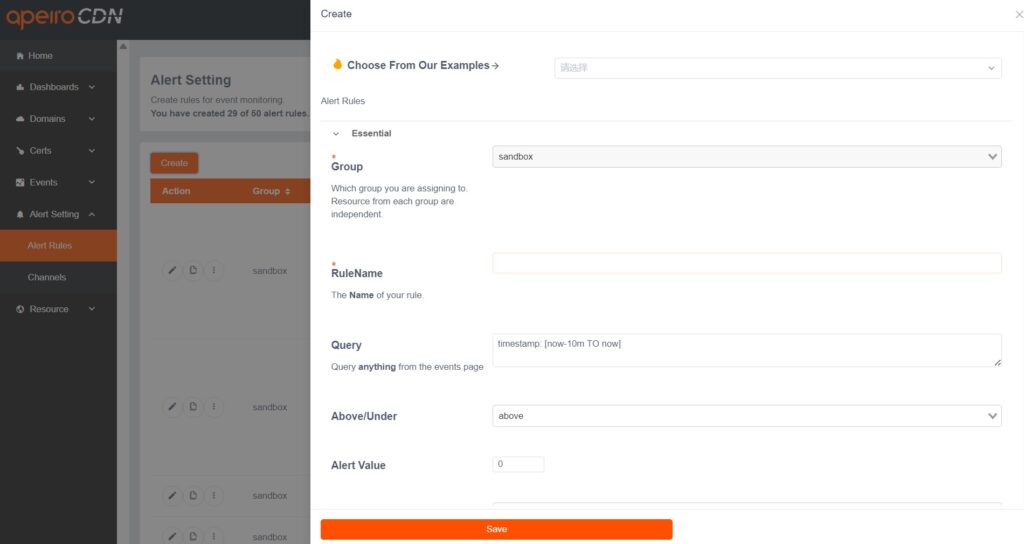
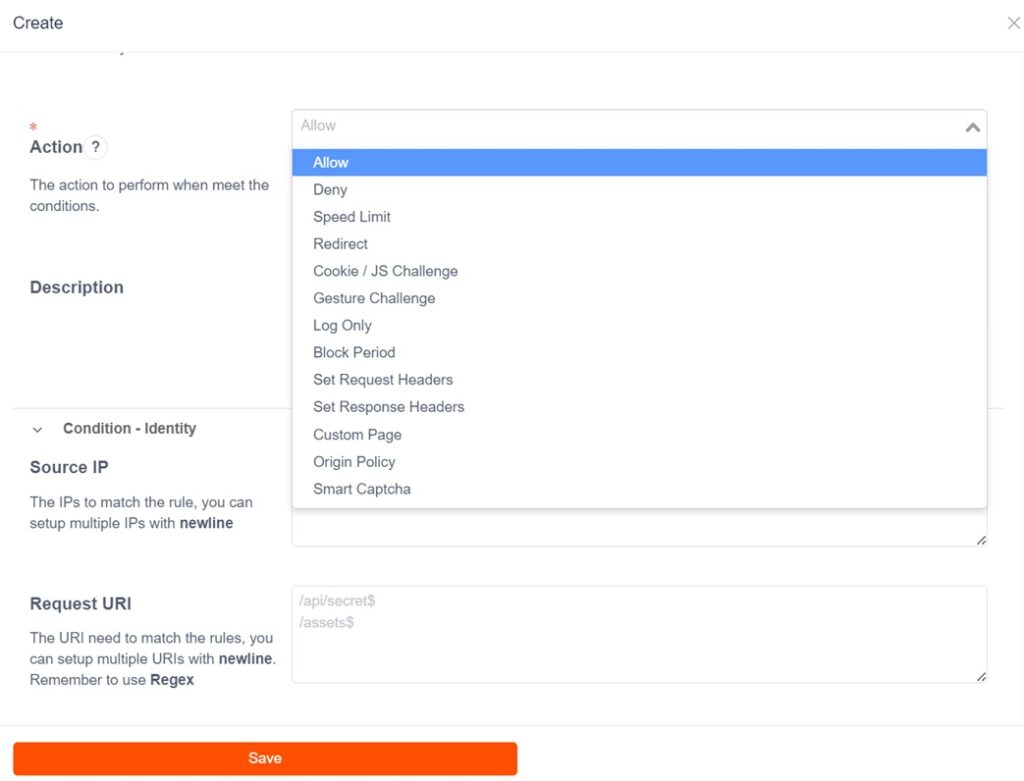
ApeiroCDN offers the most comprehensive and flexible WAF rule configurations in the industry, enabling the realization of flexible defensive strategies that have since become mainstream in website security. The impact of malicious traffic on websites can be minimized through various intensity of blocking.
In addition, ApeiroCDN provides Tb-class scrubbing center to address L3 and L4 DDoS attacks not limited by duration and scale. Most importantly, ApeiroCDN’s 24/7 security operation center (NOC) guarantees “real people and real-time communication” at all times. With real-time monitoring platform, log and flexible WAF rule settings, our professional staff can take defensive actions immediately. Our comprehensive website security ensures your website users can always enjoy optimal service experience.
⬛ Recommend: Apeiro8’s Bespoke CDN Services: Where Speed Meets Security