Exploring Botnets: Mechanisms, Varieties & Defense Strategies
 Back
Back
Launching DDoS attacks with botnets is effortless, causing immense damage through spamming, data theft, and service disruption. Defense alone is inadequate, learn the vital significance of utilizing CDN logs and alert mechanisms!
What Is a Botnet? Anyone Can Be a Victim
Botnet is a term used to describe a collection of network-connected devices that have been compromised by hackers, computer viruses, or Trojan horse programs. These compromised devices allow malicious individuals to remotely control them through Command & Control (C&C) and launch attacks, forming a “Botnet”.
Botnets are not limited to computers connected to the Internet but also include smartphones, home routers, network cameras, and other devices. With the growing popularity of Internet of Things (IoT), the number of network-connected devices has increased, making it easier to construct Botnets and increasing the risk of ordinary users’ devices being infected by Botnets.
Terrifying Botnet: Unnoticeable Infection Awaits!
“Botnet”, also known as a “zombie network”, derives its name from its characteristics. Typically, regular users are unaware if their devices have been infected, as the infection is not as apparent as with common computer viruses or ransomware, where users may notice abnormal behavior or encounter issues such as locked files. In a botnet, infected devices continue to operate normally without significant impact on system performance. In this sense, the infected device resembles a “zombie”: outwardly there may be no discernible differences, but the system is already compromised and under the control of malicious hackers.
⬛ Recommend: CDN Architecture: Exploring Different Architectures and Benefits
Botnets: Attacking and Mining Cryptocurrencies!
Devices infected and controlled by hackers can initiate various malicious attacks, evolving alongside technology. From mass spam emails to mining cryptocurrencies like Bitcoin, botnets are versatile. Some hackers use them for personal gain.
Distributed Denial of Service Attack (DDoS)
Most botnets are capable of launching DDoS attacks. They overwhelm the attack target with a massive volume of requests from infected devices, rendering it unable to respond to legitimate traffic. These attacks also consume significant amounts of bandwidth, further impeding the target’s ability to function properly.
Massive Spam Message Distribution
The dissemination of mass messages can be a service purchased by individuals with malicious intentions to transmit large volumes of messages. Furthermore, botnets themselves send out extensive phishing emails, tricking users into opening attachments and infecting additional devices.
Stealing Data
Hackers can steal sensitive information from infected devices in the botnet, including account credentials, passwords, credit card details, and stored data.
Botnet Mining
There was an example of a botnet called ZeroAccess that utilized infected devices for Bitcoin mining and other malicious activities to generate profits. Researchers have estimated that these malicious activities could yield annual profits of tens of millions of U.S. dollars.
⬛ Recommend: WAF (Web Application Firewall) vs. Firewall: Explained
Botnet, DDoS Attacks and Key Events
Botnets and DDoS attacks are closely interconnected, as the ability of botnets to control multiple devices simultaneously aligns perfectly with the principle of DDoS attacks.
Mirai Botnet
Since 2016, the Mirai Botnet has gained global attention. Renowned cybersecurity expert Brian Krebs’ website faced a massive 620Gbps DDoS attack by the Mirai Botnet. Krebs had been documenting attacks on his website since 2012, and this particular attack was three times larger than any previous ones.
OVH, a renowned managed server hosting in France, publicly reported a Mirai Botnet DDoS attack on its customers, estimating that over 145,000 devices launched an attack reaching a staggering 1.1Tbps per second, lasting for approximately seven days.
The DNS service provider Dyn experienced a 1.5Tbps attack, resulting in the denial of services for major websites like Airbnb, Github, HBO, Netflix, Twitter, PayPal, and Reddit.
These examples highlight the significant magnitude of DDoS attacks initiated by botnets. It is crucial not to underestimate them, as anyone with basic computer skills can create a botnet using source codes released by original authors and launch DDoS attacks at will.
⬛ Recommend: China CDN Solution: Pros and Cons of CDN services for China
How to Prevent Infection from Botnets?
No one wants their devices to become part of a botnet. Here’s how to avoid device infection:
1. Avoid using default passwords and use strong, complex passwords
Default passwords and common, easy-to-guess passwords are vulnerable to brute-force attacks by malware. Using strong and unique passwords enhances the security of your devices.
2. Apply system and firmware updates promptly
Device updates often include fixes and prevention measures for known vulnerabilities, not just new features. Applying updates promptly protects your devices from exploitation by malicious actors.
3. Avoid accessing unfamiliar websites and software
Phishing websites and free pirated software can hide potential risks. To safeguard your devices, it’s important to exercise caution and develop safe browsing habits.
How to Prevent Botnet Attacks?
Evolution of botnets has become an unstoppable ecosystem. Even if we can protect our devices from infection, it may not prevent our hosted websites or servers from being targeted by botnet attacks. Is there a way to prevent such attacks? Here are some suggestions:
- Verify firewall configurations and check for any unnecessary open network services and ports.
- Ensure that defense systems have regular system and firmware updates and confirm that attack detection databases are up to date.
- Regularly monitor network devices for any unusual activities.
- Ensure that network defense mechanisms are functioning properly and consider acquiring additional devices for mitigating attacks if necessary. Alternatively, consider using third-party services for DDoS mitigation.
⬛ Recommend: What is DDoS Attack? Definition, Attack Types, and OSI Model
Defending DDoS Attacks: Utilizing CDN Logs and Alerts
DDoS attacks are increasingly common and challenging to defend against. That’s why more and more websites are turning to defensive CDN services, solving both website acceleration and network attack issues. However, DDoS defense goes beyond relying solely on popular tools like scrubbing centers and WAF. Many website security professionals may not realize that leveraging logs and alert mechanisms is also a crucial weapon in preventing DDoS attacks.
Full Event Recording: Every Piece of Information Matters
In the Log, you can view comprehensive information for each visit, including domain, URI, IP, country, triggered WAF rules, HTTP code, request headers, request time, upstream response time, and more.
HTTP code, request time, upstream response time, and upstream status help you determine if user visits are normal and if the server responses are as expected. By examining any anomalies in IP and headers, and monitoring the incoming visits on the dashboard, you can identify any abnormal traffic.
With detailed request information and the expertise of cybersecurity professionals, you can gain a comprehensive understanding of the attack situation and proactively prevent it.
⬛ Recommend: WAF Guide: Attack, Defense, and Deployment Strategies
Use Filter to Analyze Abnormal Traffic
In the Log, you can use “Filter” feature to find the specific information you need. For example, you can search for relevant details such as the visited domain, URI, client IP, and headers that meet certain criteria.
For instance, some abnormal requests may lack common headers like “accept-encoding,” “accept-language,” or “user-agent.” These headers are typically present in regular browser requests. If you notice a significant number of requests without these headers or with abnormal header contents, consider setting up WAF rules to block them.
Furthermore, you can examine the country of origin for source IPs to identify any abnormal attacks. If most of your legitimate traffic originates from Asian countries, but you observe abnormal traffic coming from European or American countries, it may be worth considering restrictions on access from those regions.
Real-Time Blocking of Layer 7 Attacks Using Alert Mechanisms
When using ApeiroCDN, you can stay on top of Layer 7 attacks by configuring alert settings.
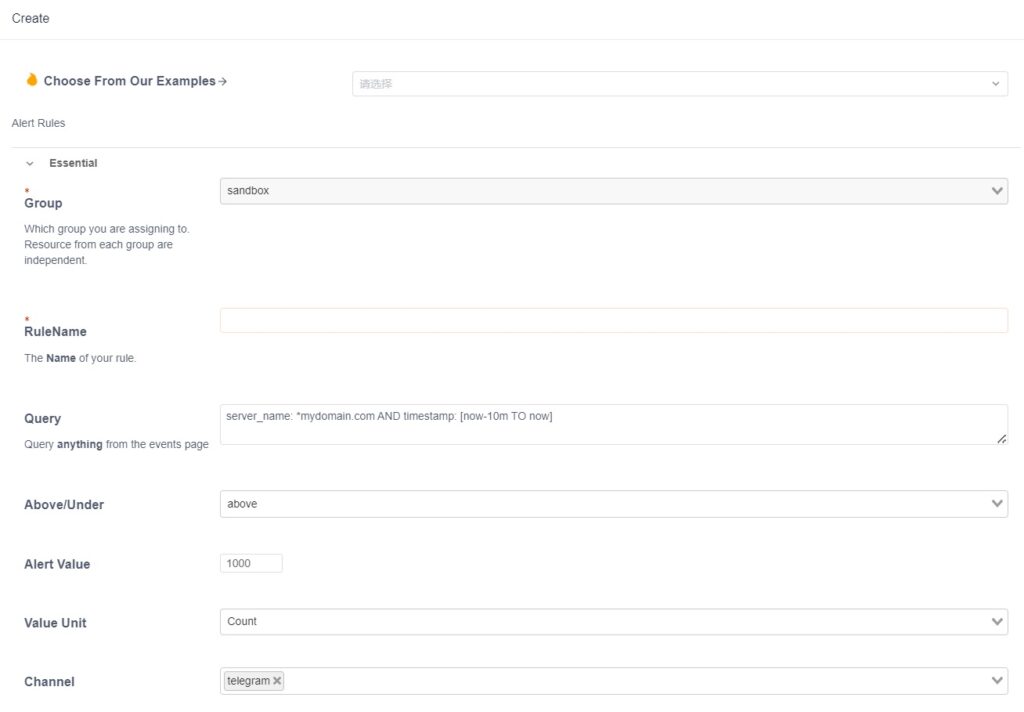
Taking the image above as an example, we can set up an alert that triggers when a domain receives more than 1000 visits within a 10-minute timeframe. Once the threshold of malicious visits is reached, you will be notified.
Upon receiving the alert, you can monitor the dashboard and check the log to analyze attack trends and identify any unusual log entries. You can then set up WAF rules to block the attacks.
By using the search function on the dashboard, you can easily find domains targeted by malicious attacks and view detailed information such as visit count, source IP, and HTTP code. For more comprehensive visit records, the log provides access to detailed information and request headers, allowing you to understand the attackers’ attack patterns.
⬛ Recommend: Choose a CDN Vendor: The Best Technical Questions to Ask
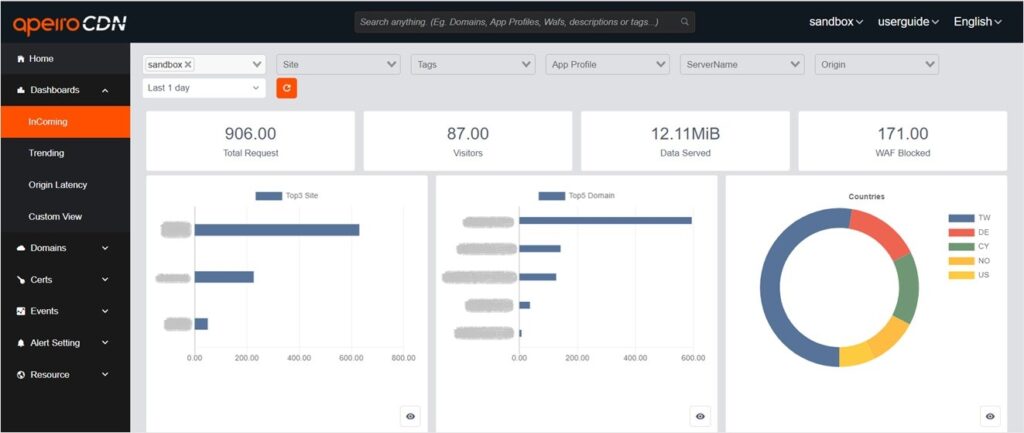
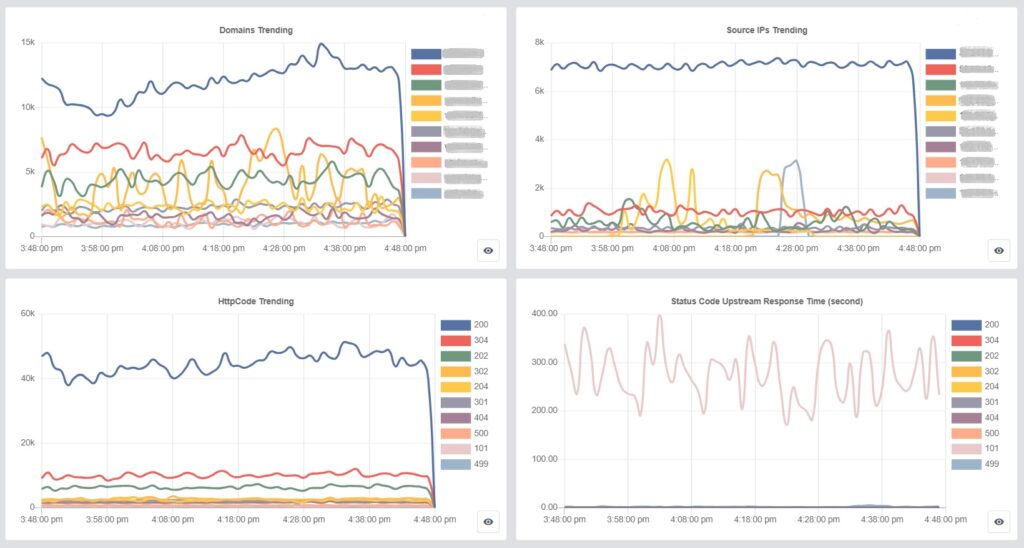
DDoS attacks are unpredictable and constantly evolving. That’s why it’s crucial for administrators to set up early warning alerts for abnormal traffic. By detecting and blocking traffic anomalies in real-time, you can ensure that your users always have the best experience.
⬛ Recommend: What is DDoS Attack? Definition, Attack Types, and OSI Model