CDN Architecture: Exploring Different Architectures and Benefits
 Back
Back
Did you know that the speed of websites for major streaming services, medical, financial and game industries are related to CDN? The CDN has evolved from its basic structure into different product types that correspond to the needs of different websites. This article will explore the advantages of CDN based on its three primary demand factors: website acceleration, cybersecurity and acceleration in China, as well as answering some key questions.
- What is the website acceleration architecture of CDN?
- What is the CDN architecture with “DDoS defense” configuration?
- Do we need to use a special CDN when website users are in China?
⬛ Recommend: What is DDoS Attack? Definition, Attack Types, and OSI Model
CDN Architecture: Nodes and Caching for Website Acceleration
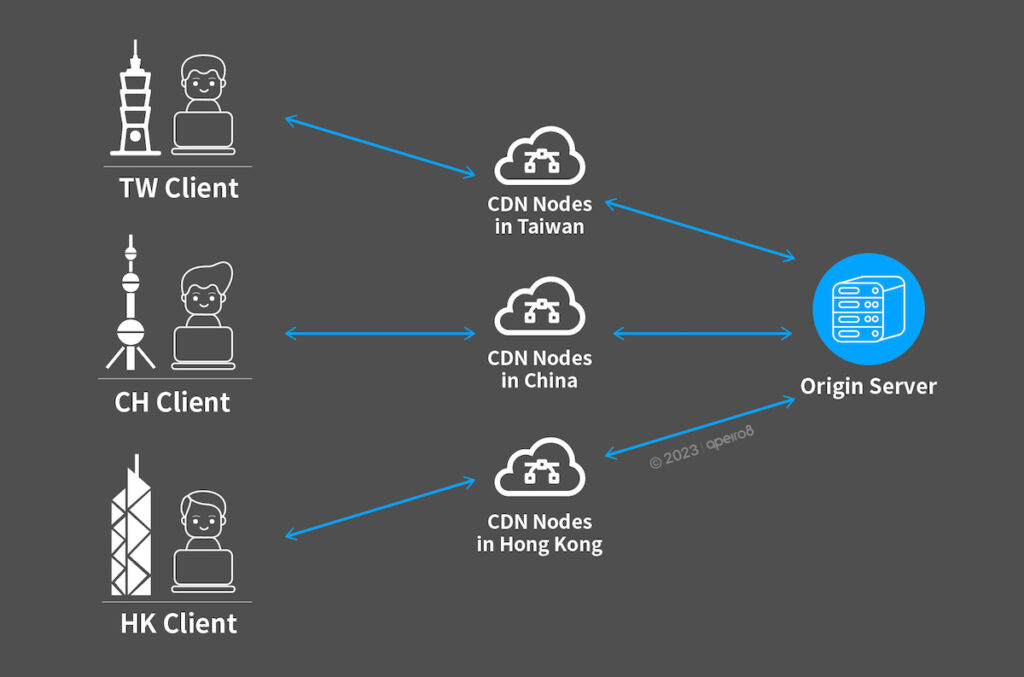
CDN was born out of the need to deliver website content faster to the website users. Contents are delivered from CDN nodes (edge servers) located throughout the world, which act as intermediates between users and servers that “shorten” the distance between requesters and service providers. The underlying principle is as follows: when users send requests to the website, the CDN can compute the most optimal (nearest) edge (node) to the user, and deliver the contents cached on the edge to the user, accelerating the content delivery and optimizing user experience.
The process of CDN caching is as follows:
1. Website User Sends a Request to a Website
After the user sends a request to the website, DNS resolves the website domain of the user’s request and returns an IP address (IP address of the CDN).
2. Obtains IP address of the website (IP address of CDN)
The DNS informs the user the IP address of website (in reality the IP address of the CDN node), the user will send a request to the IP provided by DNS, directing the request to the corresponding destination.
3. CDN Nodes Respond to User Requests with Cached Content
Upon receiving a request, the node verifies if the requested content is already cached on the node.
If yes: The node responds to the website user with the cached content, and the process ends.
If no: The node requests the object from the origin server, and upon receiving the response, the node determines whether to cache it and then responds to the website user, concluding the process.
⬛ Recommend: What is CDN? Advantages, Trends of Content Delivery Networks
CDN Architecture and Services with DDoS Protection
DDoS attacks are becoming increasingly frequent and varied, posing a threat to every enterprise. As an intermediary between users and origin servers, CDN offers the advantage of hiding the origin server, making it an excellent defense position against DDoS attacks. Consequently, more and more websites are adopting CDN services with advanced defense strategies, including DDoS scrubbing centers, WAF protection, 24/7 monitoring, real-time technical support, and all-in-one CDN management platforms.
1. 24/7 Monitoring & Immediate Response to Attacks
Taking ApeiroCDN as example, we have a service team that operates 24/7 to manage domains of customers. If there is an issue with the website, a real person is always on hand to handle issues and stop attacks as they occur, protecting the origin servers of the corporations’ websites.
- Monitor abnormal requests on the websites and configure appropriate defensive rules
- Assist in configuring domains
- Assist in application of domain certificates
- Assist in configuring CDN defensive functions
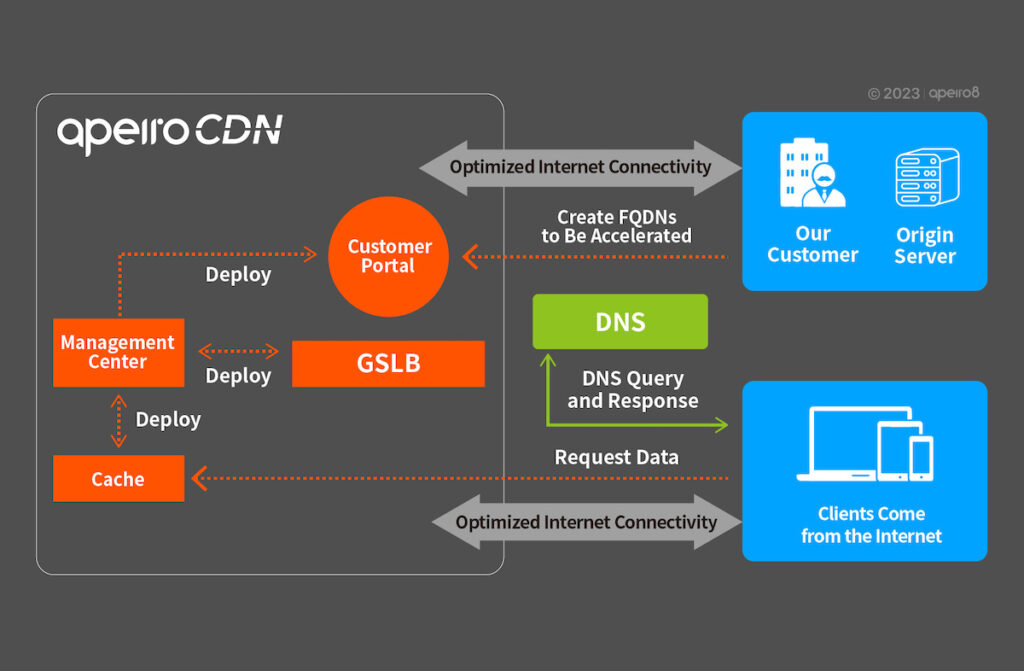
The CDN service architecture of ApeiroCDN offers excellent user experience and customizable acceleration conditions, as shown in the figure below. The FQDNs (domains) configured by the customer will be deployed on the CDN. After the domain is mapped to the CDN, the ApeiroCDN services become available to use. Clients (End-users) can access the content by resolving the Load Balancer IP through the DNS system. If the requested object is cached, it will be directly served to the client.
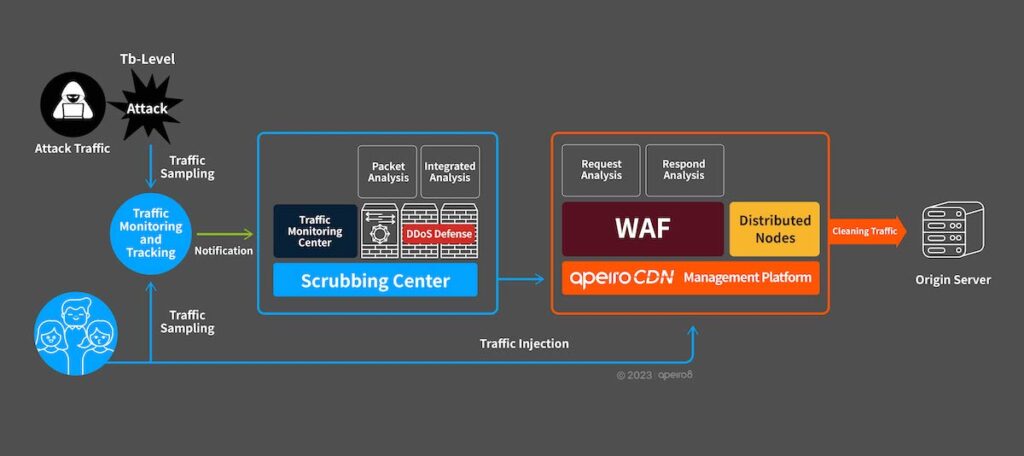
2. Multi-layer DDoS Defense Mechanisms Protect the Origin Server
The DDoS defensive services of ApeiroCDN can automatically detect abnormal traffic and redirect them to the scrubbing center, preventing the malicious traffic from impacting normal website users. In addition, ApeiroCDN can also painlessly transfer traffic; Even if the incoming traffic are from HK route, they can be redirect to TW nodes by back-end manipulation, ensuring robust redundancy. In case of exceptionally high attack traffic affecting specific routes, ApeiroCDN can quickly switch routes to maintain uninterrupted user services.
- Scrubbing Center
The routes used by the ApeiroCDN support scrubbing center. If the threshold value of the scrubbing center is triggered by an attack on the user’s website, the traffic will be redirected into the scrubbing center for filtering. This helps alleviate the heavy attack load on both CDN nodes and origin servers at the same time. - Comprehensive Request Log and Flexible WAF Rules
If the attack traffic do not trigger threshold value of the scrubbing center, or the attack pattern is too specialized to be scrubbed, ApeiroCDN provides comprehensive request log records for website administrators to analyze abnormal traffic and implement customized WAF defensive mechanisms on the domains under attack to filter abnormal traffic. - Clean Traffic and Service Acceleration
The traffic that arrive at the origin servers are “clean”, ensuring an optimal service experience for website users.
⬛ Recommend: CDN Tutorial: Reverse Proxy Server Principles & Advantages
3. Flexible WAF Rule Configuration for Versatile Defense
How can an enterprise defend itself against increasingly diversified malicious attacks? Aside from sending large requests from a single IP, the attack patterns these days also include types such as multi-IP to single User_Agent, multi-IP to multi-User_agent, and multi-IP to single header content. To counter these attack types, a CDN that can flexibly deploy defenses is necessary.
ApeiroCDN allows website administrators to customize defensive rules, increasing the precision of defensive strategies and lowering false intercepts by configuring IP blockage, headers and request conditions. In addition, it is possible to set up an observation mode where, in uncertain situations on how to block attacks, you can test and simulate the results of the configuration. This feature can filter out 90% of abnormal traffic.
When the signature of attack is very evident, such as unique headers in the requests, discrepancies between headers and protocols, fixed sources, fixed IP addresses being accessed, or request methods not matching the actual behavior, the WAF on the CDN can perform precise blocking. This not only avoids impacting normal users but also effectively blocks the attacks, achieving the desired protection.
ApeiroCDN’s WAF Offers Diverse Defense Modes in Its CDN Architecture:
- Speed Limit
Keeps the request volume within reasonable range to prevent service outage caused by large requests from a single IP. - Smart Captcha
Use various types of Captcha to filter bots. - Log Only
When using the “Log Only” mode for observation, if the results meet expectations, the action taken by the WAF rules can be modified. For example, by observing whether the current set of rules successfully matches abnormal traffic in “Log Only” mode, once the majority of abnormal traffic matches the rule, the action can be changed to “Deny”. - Allow (whitelist)
- Deny (blacklist)
- Redirect
- Js Challenge (prevent bots)
- Gesture Challenge (blocks botnet)
- Block Period
- Set Request Headers
- Set Response Headers
- Custom Page
- Origin Policy (provides IP hash/Round Robin/Weight origin modes)
“There is no extraordinary defense, only exceptional configuration. As long as the WAF is highly flexible and operates in coordination with various modes, it can achieve high efficiency and effectiveness in protection.”
Diversified China Acceleration Routes for Uninterrupted Services
CN2 routes in China are expensive and not affordable for all businesses. However, if users in China access websites through overseas routes, the speed is significantly slower. Since China has a large user base and market, it is important to provide China-specific routes to enhance the user experience for your website. By offering China routes, ApeiroCDN nodes accelerate request speeds and reduce user drop-off and complaints caused by slow speeds, ensuring a high-quality experience for users in China.
⬛ Recommend: China CDN Solution: Pros and Cons of CDN services for China