Identifying L7 DDoS Attacks(part1): Monitoring and Analyzing
 Back
Back
This article is divided into 2 parts.
Previously in the article “Exploring Botnets: Mechanisms, Varieties & Defense Strategies” the importance of logs in defending against DDoS attacks was mentioned. This included information of requests that CDN services need to provide to clients. By recording detailed information about all requests, an all-in-one CDN management platform can further offer various visualized reports, helping website security personnel accurately monitor minute-by-minute traffic fluctuations and CDN defense performance.
Administrators can find these charts from the dashboard, which will be discussed in the following sections:
- Why is the dashboard an essential tool for stopping L7 attacks?
- What are the essential visual charts?
- How to use the charts to determine the presence of abnormal traffic (DDoS attacks)?
- How to check CDN caching performance?
- How to understand the status of CDN defenses (WAF)? (Part 2)
- What is Origin Latency? (Part 2)
- The importance of “custom” dashboard (Part 2)
DDoS Attack Types: 4 Essential Dashboard Metrics
Protocol Attacks: Target vulnerabilities in the OSI Layer 3 and Layer 4, such as SYN flood and ICMP flood, causing server capacity overload and service paralysis.
Application Layer Attacks: Target the OSI Layer 7 and involve more complex techniques, such as constant page refreshing, login page flooding, and API abuse, leading to server performance degradation or service disruption.
For a defensive CDN with Tb-class DDoS scrubbing service, L3 and L4 attacks will be automatically directed to the scrubbing center. However, since a L7 attack is complex and sometimes difficult to detect, it requires the use of various mechanisms such as the request log, traffic trend data charts, WAF rules and alerts to determine and configure blocking rules of various intensity, precisely filter the abnormal traffic while maintaining normal website browsing experience for normal users.
In this instance, the dashboard (visual charts) of an all-in-one CDN management platform becomes an important tool for identifying L7 attacks.
⬛ Recommend: What is DDoS Attack? Definition, Attack Types, and OSI Model

L7 DDoS is Complex: Importance of Report Interpretation
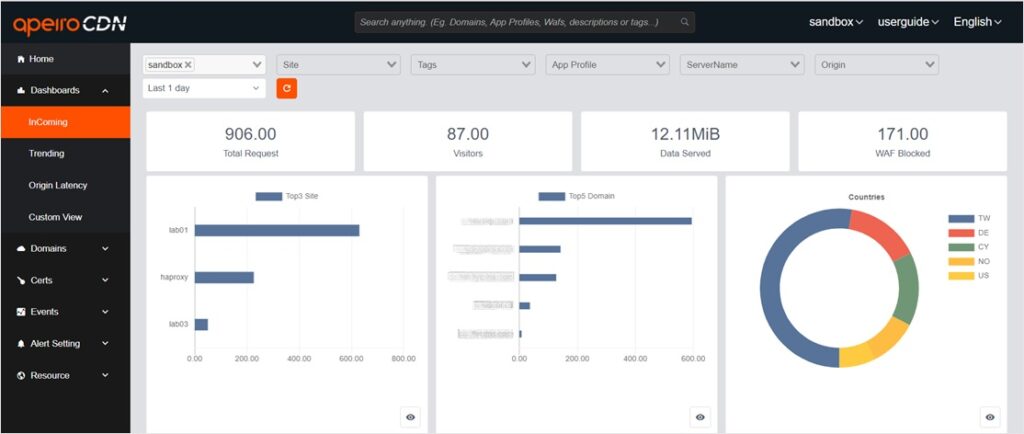
Layer 7 DDoS attacks are highly sophisticated and difficult to detect, making it challenging for automated systems to identify them accurately. Therefore, having a monitoring dashboard that integrates Layer 7 and server-related data, along with personalized data reports and interfaces, becomes crucial in effectively identifying suspicious attacks. Here are essential monitoring data on a CDN platform:
- Incoming Requests: total request volume, visitor volume, data served and WAF blocked. Use this data to determine whether an attack has occurred and the defensive outcomes.
- Trending: Domains, Source IP, Http Code, Upstream Http Code & Response Time, analyze traffic trends with these conditions.
- Origin Latency: Group Origin Latency, Origin Latency, Origin Http Health Status, check the latency and status from CDN to the origin servers with these conditions.
- Custom View: Select data, conditions, types of charts, filters to build personalized monitoring dashboard and visual charts.
Filtering for Detailed Domain Information
You can observe the following data from the monitoring dashboard by setting filtering conditions such as domains or groups:
- Total Request: the overall number of requests; for example: observe whether traffic from a specified time interval have spiked to determine presence of anomaly.
- Visitor Volume: the overall number of IPs (Unique IP); for example: whether the number of IPs to a domain is abnormal.
- Data Served: the overall data usage, average bandwidth, and cache rate, for understanding how traffic are saved for the origin servers.
- WAF Blocked: the frequency of triggered WAF rules, configured for defensive or customized purposes, which is used to check whether CDN defenses or WAF rules are effective.
⬛ Recommend: WAF (Web Application Firewall) vs. Firewall: Explained

DDoS Defense Tutorial: Analyzing Request Trends for Attacks
In general, to determine whether an attack is L7, the data to be examined from the all-in-one CDN management platform is the incoming request traffic, which include the following: total request trend, Top 5 domains, Top 3 sites, countries, WAF blocked and WAF types. Aside from DDoS attacks, one of the most important tasks of CDN is acceleration service, and the critical indicator for understanding CDN performance is its “caching” performance. The following will describe how CDN users can interpret data on incoming requests to discover abnormal traffic and evaluate caching strategies.
Identify DDoS Attacks from Incoming Request Charts
Chart of total requests: analyzing “Total Requests Line Chart” to identify abnormal high peaks in average request volume.
- Top 5 Domains: Analyze Top 5 visited domains of a specific time period to identify the domain with abnormal request volumes.
- Top 3 Sites: Review the top 3 sites in terms of request volume and compare them with the top 5 domains to quickly determine if the domain’s corresponding site is abnormal.
- Countries: By analyzing the countries chart, you can identify the originating countries of each IP address and determine if there is a need to restrict requests from specific countries.
For example: in the charts, the first domain has much higher traffic than other domains, therefore one should check the total request volume from this domain and compare it with historical data to see whether there are any abnormal peaks. If there are, then it could be determined as an attack. If the traffic mostly located in TW, one can then restrict the requests from TW.
⬛ Recommend: Exploring Botnets: Mechanisms, Varieties & Defense Strategies
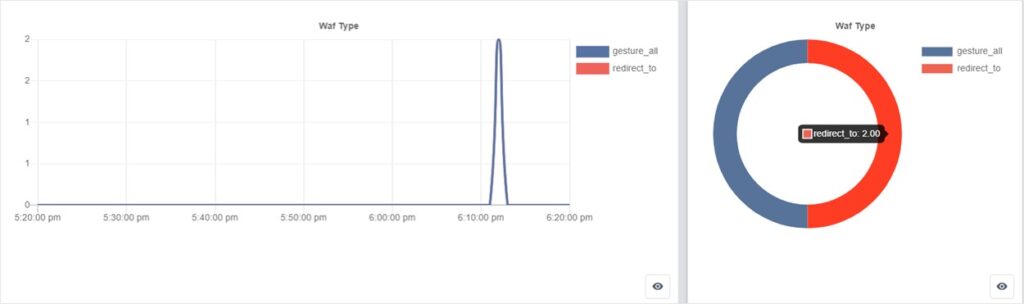
DDoS Attack Alert: Has WAF Rules Been Hit?
Determining if an attack is occurring by examining WAF blocked types to identify if any WAF rules have been triggered.
WAF Type Trending: the line chart shows the WAF rules triggered data at each time point within the filtered time intervals, such as: the hit WAF rules by seconds within 1 hour; you can also switch to check the raw data.
WAF Type Ratio: The triggered WAF types within the selected time period can be observed from the donut chart, indicating the proportion of interceptions by different WAF rules within an hour. The exact data can also be viewed using the “view” button in the bottom right corner.
For example: the activation of a specific WAF rule can be determined by examining the WAF Type Trending and WAF Type Ratio charts, indicating that the WAF rule has been triggered and is effectively in place.
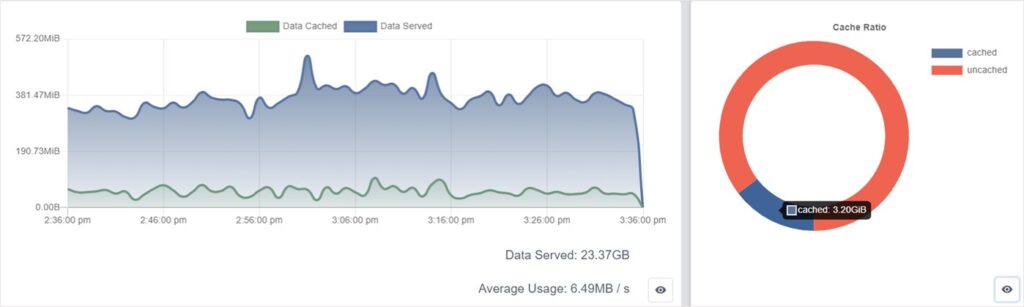
Data Usage and Cache Rate Analysis
Data Served & Data Cached: the line chart compares the differences between the two; you can see how much traffic the CDN has saved for the origin servers.
- Data Served: the overall data usage of the client side (all domains of a single customer).
- Data Cached: the traffic that is saved when data is returned to the user with caching and without accessing resources from the origin servers.
- Conclusion: Data Served – Data Cached saved = traffic used when CDN fetched the data from the origin servers.
- Cache Ratio: the donut chart shows the data that is cached or not cached. The type of CDN cache can be reference from object configuration.
- Cached: deep blue indicates the data that has been cached by the CDN.
- Uncached: deep red indicates data that is not cached by the CDN.
For example: by checking the overall cache traffic of a domain, you can see that some of it remained uncached.
Content of Part 2:
- How to understand the status of CDN defenses (WAF)?
- What is Origin Latency?
- The importance of “custom” dashboard
⬛ Recommend: WAF Guide: Attack, Defense, and Deployment Strategies